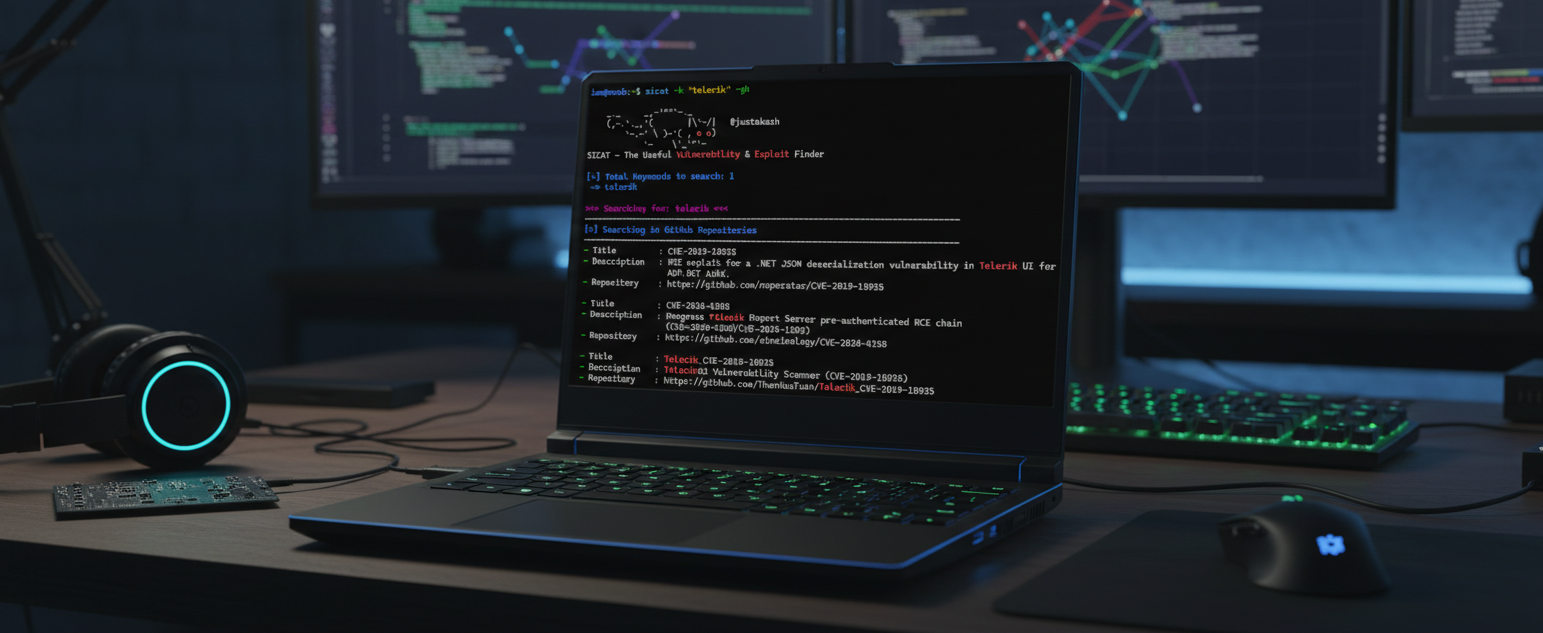
SICAT is a powerful tool designed to aggregate and search for vulnerabilities and exploits from multiple high-profile sources. It simplifies the reconnaissance phase by automatically checking reputable databases based on keywords, Nmap scan results, or detected web technologies.
This version of SICAT introduces significant enhancements over the original implementation:
- New GUI: A stunning, dark-themed web interface accessible via
--web-interface. - Hacker Aesthetics: Features animated ASCII art, "Matrix-like" loading screens, and a minimalist search engine feel.
- Interactive: Real-time visual feedback during scans and easy-to-use toggle chips for source selection.
- HTML Reports: Generates detailed, interactive HTML reports (
-r) using DataTables. - Features: Sortable columns, search filtering, pagination, and a clean, responsive design matching the CLI's dark theme.
- Auto-Discovery: Automatically builds search keywords from:
- Nmap Scans: Live IP scanning (
-nmap) or XML file parsing (-nmap-file). - Web Technology Detection: Wappalyzer integration (
-web) to identify running stacks (CMS, Server, Frameworks).
- Nmap Scans: Live IP scanning (
- Keyword Builder: Deduplicates and refines keywords for more accurate search results.
Expanded search capabilities across 8 major databases:
- Exploit-DB: Classic exploit archive.
- NVD NIST: National Vulnerability Database.
- CVE.org: Official CVE records.
- GitHub: Public repositories and PoCs.
- Nuclei Templates: Community-curated vulnerability templates.
- Wordfence CVE: Nuclei templates specifically for WordPress vulnerabilities.
- Metasploit Framework: Replaceable modules.
- NSE Scripts: Nmap Scripting Engine scripts.
- Refined CLI: Cleaner argparse help, better console output tables, and silent mode (
-s). - Performance: Multithreaded scanning structure (where applicable) for faster gathering.
Quickly install dependencies and add sicat to your system path using the installer script. This supports standard Debian/Ubuntu, Kali (fixes PEP 668 errors), Fedora, Arch, and MacOS environments.
# Clone the repository
git clone https://github.com/justakazh/sicat.git
cd sicat
# Make script executable
chmod +x install.sh
# Run installer
./install.shDouble-click install.bat or run it from the command prompt. This will:
- Check for Python and Nmap.
- Install Nmap via Winget if missing (requires Admin).
- Install Python dependencies.
- Verify the
sicatcommand is available in your PATH.
You can also run SICAT in a container to avoid dependency issues.
-
Build the image:
docker build -t sicat . -
Run the container:
docker run --rm -it sicat -k "wordpress"
# Install system-wide
pip install .
# Or for development
pip install -e .Some modules (like GitHub, Nuclei Templates, Wordfence CVE) require a GitHub Personal Access Token to avoid API rate limits.
- Auto-Generate: Run
sicatonce, and it will create~/.sicat/config.json. - Edit: Open
~/.sicat/config.jsonand add your token:
{
"gh_token": "YOUR_GITHUB_ACCESS_TOKEN"
}Basic Search:
sicat -k "WordPress 5.8"Search Specific Sources:
sicat -k "Apache Struts" -edb -gh -nucleiGenerate HTML Report:
sicat -k "Joomla" -o results.json -r report.htmlAuto-Scan via Nmap:
# Scans the target IP with Nmap first, then searches exploits for found services
sicat -nmap 192.168.1.10 -edb -cveAuto-Scan via Web Detection:
# Detects technologies (e.g. Laravel, Vue.js) and searches exploits for them
sicat -web https://example.com -gh -nvdLaunch the web GUI to run scans from your browser:
sicat --web-interfaceNavigate to
http://localhost:5000in your browser.
-u, --update Update all local databases and resources
-k KEYWORD Specific keyword to search for (e.g. 'WordPress 5.8')
-nmap TARGET Target IP for live Nmap scan
-nmap-file FILE Path to Nmap XML file
-web URL Target URL for Wappalyzer scan
--web-interface Start the web-based GUI interface
-edb Enable search in Exploit-DB
-nvd Enable search in NVD NIST Database
-cve Enable search in CVE.org
-nuclei Enable search in Nuclei Templates
-wcve Enable search in Wordfence CVE Templates
-gh Enable search in GitHub Repositories
-msf Enable search in Metasploit Framework
-nse Enable search in Nmap NSE Scripts
-s Run in silent mode
-l LIMIT Limit the number of results per module (default: 25)
-o OUTPUT Path to save the console output
-ot {text,json} Format of the output file
-r [FILE] Generate an HTML report
Contributions are welcome! Please check CONTRIBUTE.md for a guide on how to add new sources or features.
SICAT is intended for educational and ethical testing purposes only. Usage of this tool for attacking targets without prior mutual consent is illegal. The developers assume no liability and are not responsible for any misuse or damage caused by this program.
This project is licensed under the MIT License.